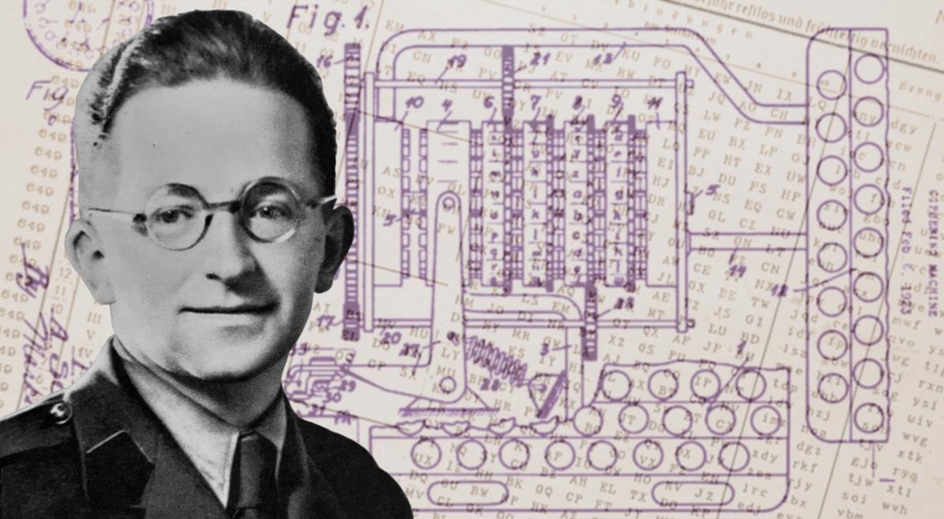
…seems like life gave me a call to action…
Introduction
Every time you connect to the Internet, you are likely to be using elliptic curves to generate the encryption key that you and the server are using. This is a unique key, and that builds on the Diffie-Hellman method, but uses the beauty of elliptic curves.
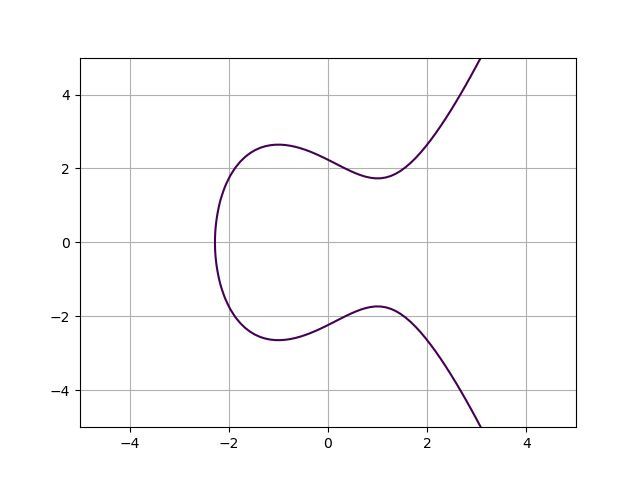
Elliptic curves should be understood by everyone who uses digital assets. Bitcoin, Ethereum would not be possible without it. Elliptic curve cryptography is a type of asymmetric cryptography that uses elliptic curves to create mathematically linked public & private keys. Your private key is what gives you access and privacy to your digital assets while the public key is the proof to anyone in the system to see. The curve used by Bitcoin and Ethereum is called secp256k1, defined by:
y^2=x^3+7.
The points along the curve is used to derive the values of public and private keys. Public-key cryptography is useful because it satisfies 2 conditions:
- It is computationally impossible to derive a private key from its public key.
- It is possible to prove ownership of a given private/public key pair without disclosing any information about the private key.
There are 2^256 combinations of public and private keys. That number is larger than the number of atoms in the observable universe. To brute force, a private key is statistically improbable which makes your private/public key pair secure and safe.
Creation of Bitcoin address from scratch
In order to create a Bitcoin address, a private key, which is a randomly generated number, is multiplied using an elliptic curve to produce a publik key. Generated public key is then put through both SHA-256 and RIPEMD-160 hashing algorithms.
1A = RIPEMD-160( SHA-256(K) )23where45A - Encrypted public key6K - Public key
The use of the SHA-256 and RIPEMD-160 hashing algorithms for the creation of a Bitcoin address gave one big advantage: shorter addresses. A public key is 256 bits long whereas, the hashed version of the Bitcoin address is 160 bits long.
As we can see, the SHA-256 hashing algorithm is a core part of the Bitcoin protocol, but it is not enough. Using additionally RIPEMD-160 is like psychopath vibe - so needed in this kind of systems.
The. World. Is. Crazy. LITERALLY.
But only the truth is interesting.
ZK Proofs
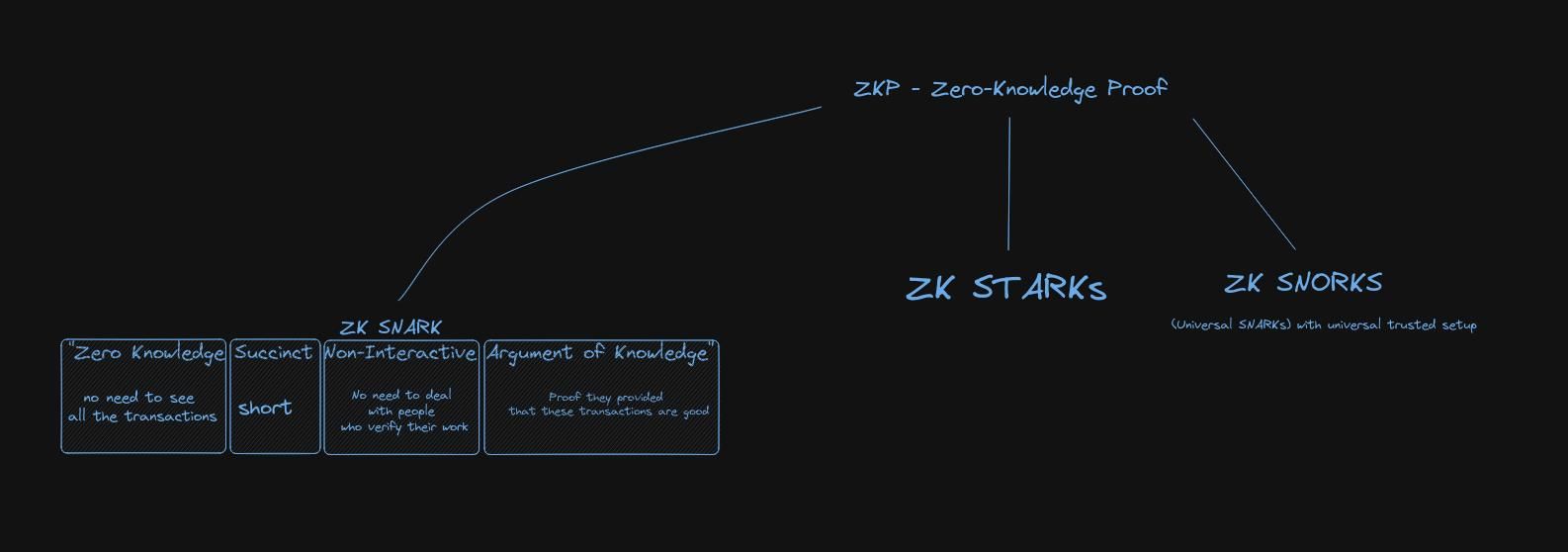
Examples of definitions of the ZK Proof:
- “A ZK Proof mathematically demonstrates to a third party (typically called the verifier) that you’ve done some computation honestly without revealing the details nor requiring recomputation.”
- “ZK Proofs are essential for web3 because they allow us to ensure correctness while maintaining privacy. For example, we might print that a financial transaction is genuine, while not revealing who paid whom or how much.”
- “ZK Proofs in blockchains are typically used for statements like this: ‘I am entitled to authorize action F because I hold a secret that satisfies requirements R’, without telling anybody the secret.”
ZK Proofs give privacy+scalability:
- Scalability: I prove I did a hard computation on some data, so the chain doesn’t have to do the work itself or store the data
- Privacy: I prove I put > $20 into a mixing pool, w/o revealing which deposit transaction was mine
Zero-knowledge proofs (zk-proofs) are a type of cryptography that allows one party to prove the validity of a statement to another party without revealing any information beyond the fact that the statement is true. These proofs are designed to ensure that the information being revealed is completely secure, and that the person providing the proof cannot be tricked into revealing more information than they intend to.
In a zero-knowledge proof, the prover demonstrates that they have certain information without actually revealing it to the verifier. The verifier can then check the proof and be convinced that the statement is true, without learning any additional information. Zk-proofs are used in many applications, including secure authentication, privacy-preserving data analytics, and blockchain-based systems.
zk-proofs: I can prove to you I know where Wally is, without showing you where Wally is..

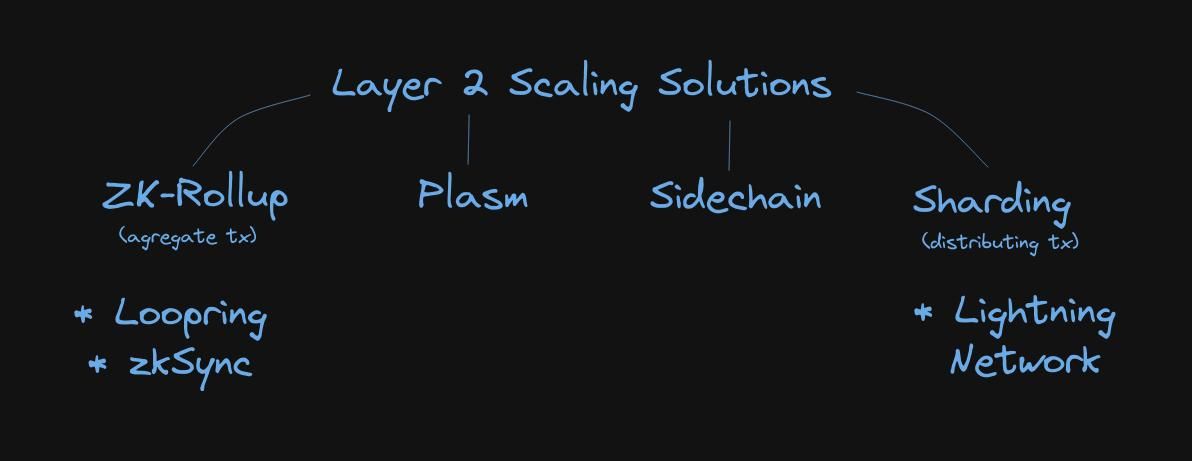
Layer 2 Scaling Solutions
Examples of commands
1openssl dgst -sha512 [FILE]2echo -n "hello" | openssl dgst -sha512
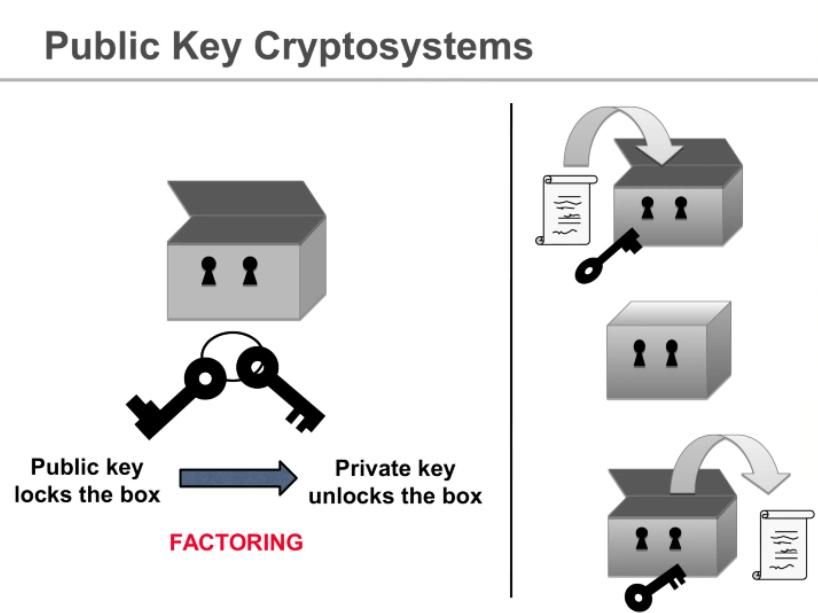
Key distribution problem
Software engineering versus cryptographers
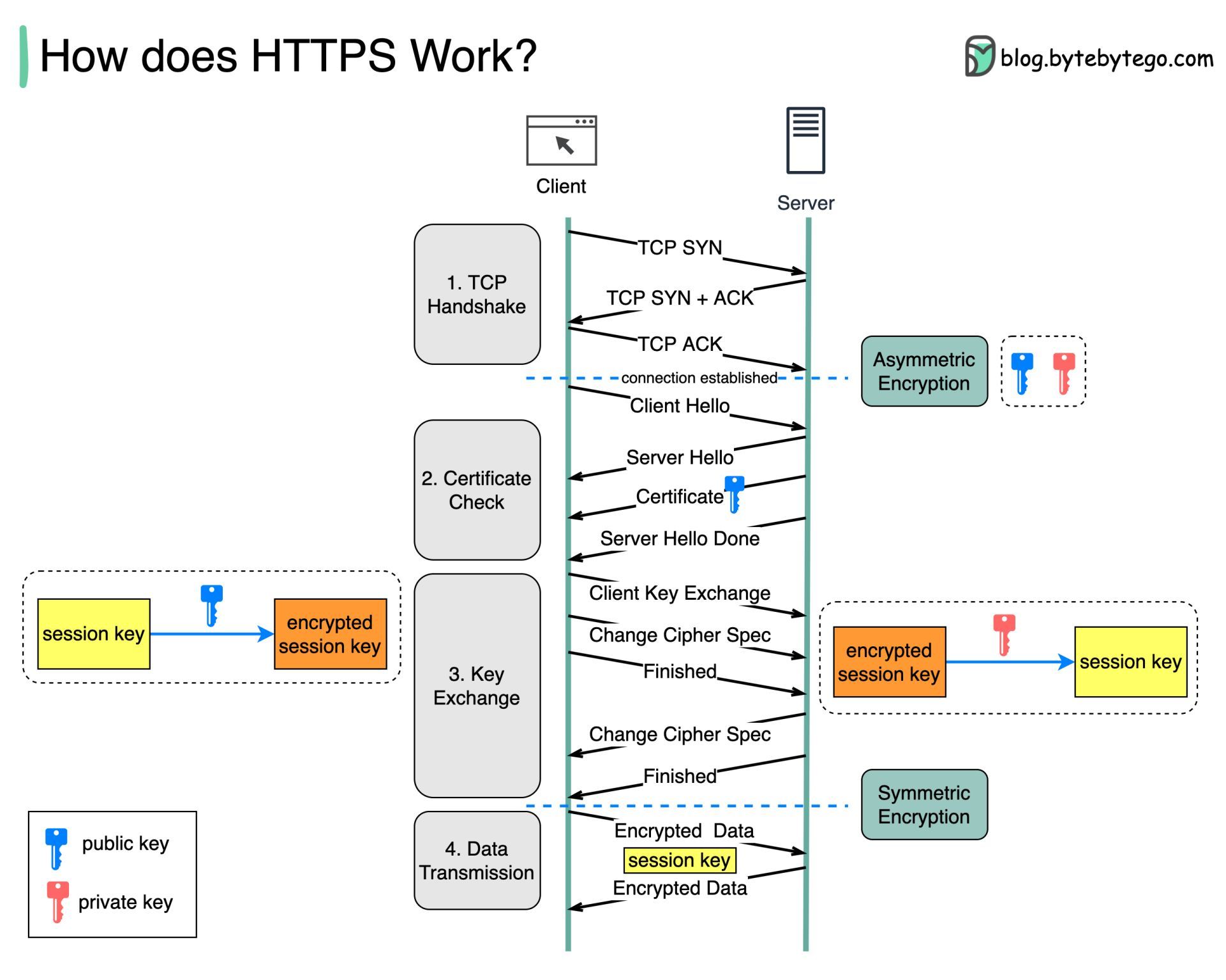
How HTTPS works?
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP.) HTTPS transmits encrypted data using Transport Layer Security (TLS.) If the data is hijacked online, all the hijacker gets is binary code.
How is the data encrypted and decrypted?
Step 1 - The client (browser) and the server establish a TCP connection.
Step 2 - The client sends a “client hello” to the server. The message contains a set of necessary encryption algorithms (cipher suites) and the latest TLS version it can support. The server responds with a “server hello” so the browser knows whether it can support the algorithms and TLS version. The server then sends the SSL certificate to the client. The certificate contains the public key, hostname, expiry dates, etc. The client validates the certificate.
Step 3 - After validating the SSL certificate, the client generates a session key and encrypts it using the public key. The server receives the encrypted session key and decrypts it with the private key.
Step 4 - Now that both the client and the server hold the same session key (symmetric encryption), the encrypted data is transmitted in a secure bi-directional channel.
Why does HTTPS switch to symmetric encryption during data transmission? There are two main reasons:
- Security: The asymmetric encryption goes only one way. This means that if the server tries to send the encrypted data back to the client, anyone can decrypt the data using the public key.
- Server resources: The asymmetric encryption adds quite a lot of mathematical overhead. It is not suitable for data transmissions in long sessions.
Random fact 1: The inventor of SHA-2 (Secure Hash Algorithm 2) is United States National Security Agency (NSA), their work was published publicly in 2001.
Random fact 2: NSA advises dropping C/C++ and moving to memory-safe languages. It’s something that large industry players were saying a long time ago. Nevertheless, it’s good to see NSA supporting the idea.

PS. In the header of the post is a picture of Marian Rejewski - the great Polish code breaker, the author of bombe decryption machine built in Bletchley Park. Marian Rejewski together with Jerzy Różycki and Henryk Zygalski developed techniques to decrypt the German machine ciphers during World War II.
If you really want to get down in the weeds
- One time pad
- Wallet from private key
- Cryptohack Challenges
- Cryptopals
- NSA urges orgs to use memory-safe programming languages
- A Graduate Course in Applied Cryptography
- A Graduate Course in Applied Cryptography, Dan Boneh and Victor Shoup
- Applied Cryptography, Fall 2019
- Rethinking National Security
- Secure Hash Standard (SHS)
- SHA-3